Exploiting Misconfigurations in Argo Workflows for Kubernetes Cluster Takeover
cve cybersecurity securityExploiting Misconfigurations in Argo Workflows for Kubernetes Cluster Takeover
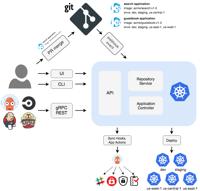
Argo Workflows, a widely-used open-source tool for orchestrating workflows in Kubernetes, has become a valuable asset for cloud-native automation. However, recent findings by Yali Mintus, a Cloud Secu … Read more
Published Date: Jan 07, 2025 (7 hours, 41 minutes ago)
Vulnerabilities has been mentioned in this article.
CVE-2024-8474 CVE-2024-31989 CVE-2024-28175 CVE-2023-40029
Go to Source